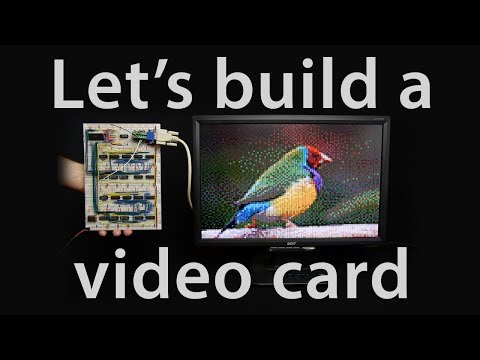
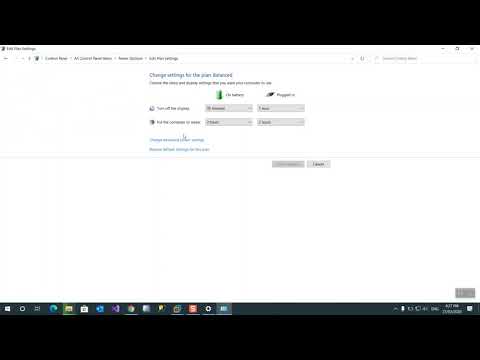
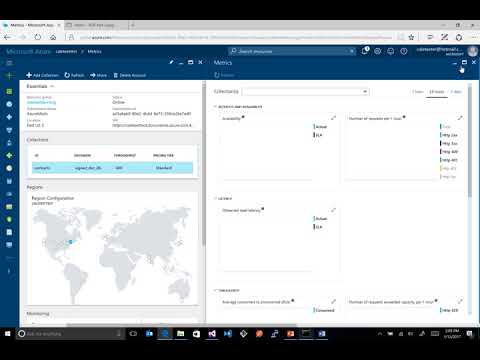
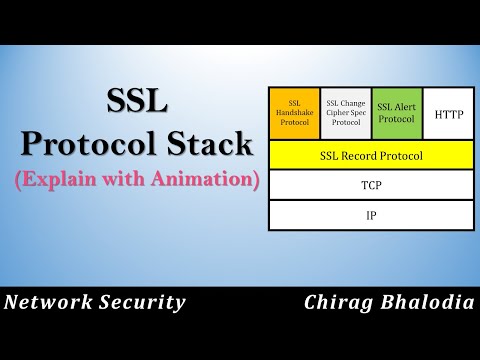
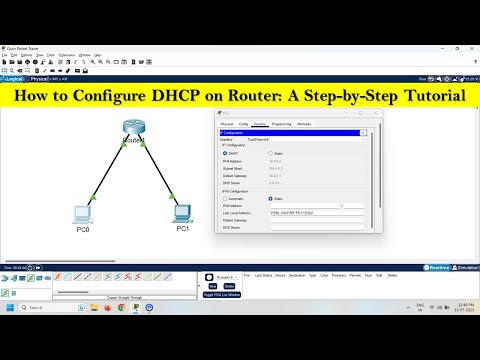
7,560 1.01%
4,620,000 2.7%
3,390,000 1.13%
116,000 2.3%
97,800 3.1%
170,000 3.82%
835,000 2.77%
123,000 3.05%
29,600 2.77%
7,880 4.73%
553,000 1.21%
134,000 2.48%
119,000 1.9%
16,900 2.48%
496,000 2.68%
3,970,000 3.56%
3,030,000 1.43%
222,000 4.18%
10,500,000 3.02%
14,700 2.35%
26,700 0.72%
6,750 3.09%
52,300 4.06%
26,700 2.97%
11,800 0.42%
760,000 1.68%