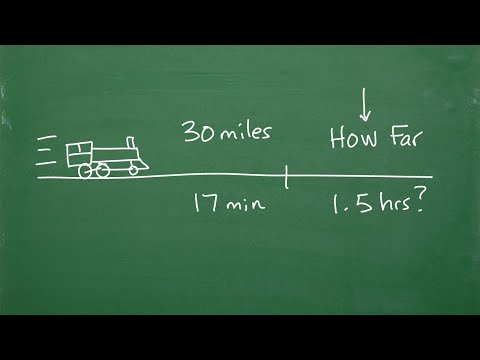
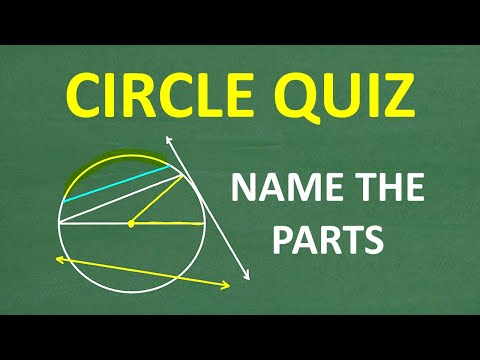
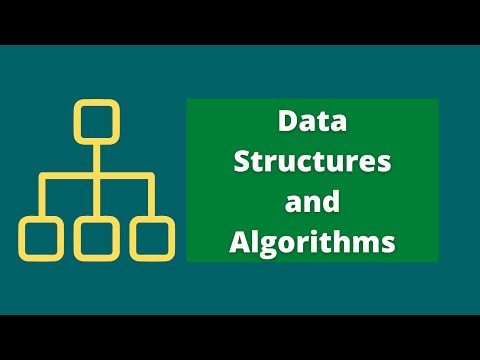
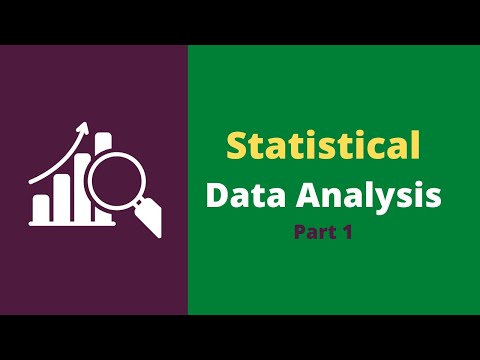
20,000 2.56%
222,000 4.18%
10,500,000 3.02%
26,700 2.97%
7,880 4.73%
154,000 2.3%
4,620,000 2.7%
260,000 2.33%
8,280 4.28%
4,070,000 2.84%
162,000 4.91%
184,000 1.43%
7,330 5.68%
47,800 3.3%
97,800 3.1%
6,680 3.57%
32,400 2.19%
531,000 1.1%
119,000 1.9%
76,500 2.09%
187,000 3.82%
220,000 2.02%
322,000 3.51%
496,000 2.68%
50,300 1.38%
801,000 3.01%