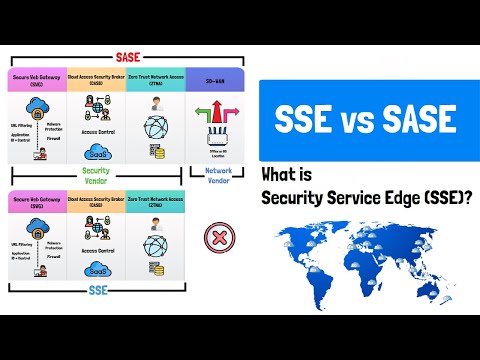
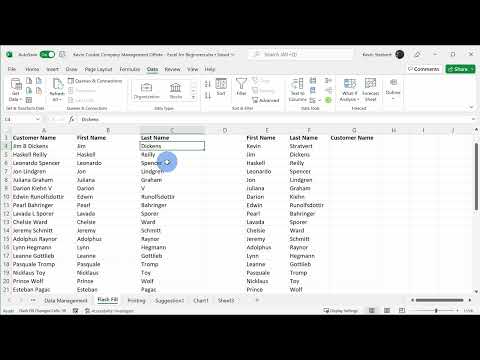
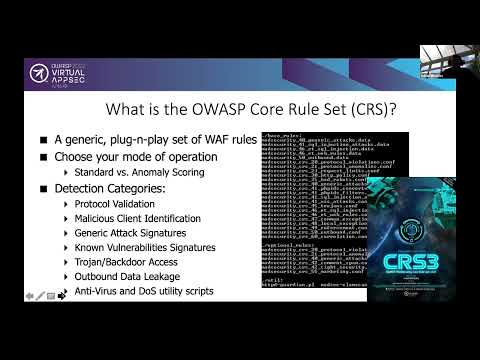
6,980 1.46%
672,000 3.58%
222,000 1.78%
164,000 2.09%
32,400 2.19%
364,000 3.05%
496,000 2.68%
801,000 3.01%
133,000 4.71%
342,000 1.71%
10,500,000 3.02%
8,380 4.53%
184,000 1.43%
47,100 2.42%
13,700 2.85%
50,100 2.39%
477,000 2.37%
14,500 1.49%
205,000 2.23%
225,000 2.35%
85,300 10.27%
1,840,000 3.59%
1,080,000 2.7%
474,000 4.75%
661,000 2.65%
50,300 1.38%