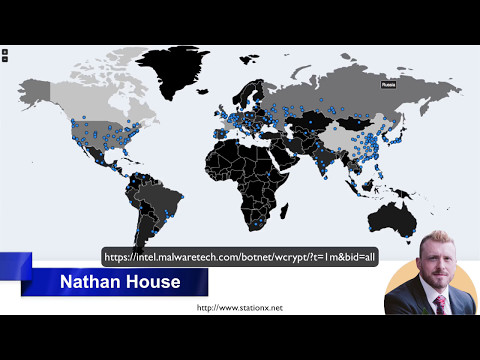
9,270 2.46%
2,040,000 2.68%
3,030,000 1.43%
496,000 2.68%
474,000 4.75%
3,390,000 1.13%
672,000 3.58%
10,500,000 3.02%
637,000 2.45%
63,400 1.8%
1,540,000 2.64%
4,620,000 2.7%
39,200 0.76%
97,800 3.1%
353,000 2.17%
9,190 1.53%
760,000 1.68%
54,400 1.3%
154,000 2.71%
86,500 2.05%
7,100,000 2.66%
137,000 2.97%
3,360,000 1.48%
157,000 2.62%
2,070,000 2.26%
7,060 2.2%