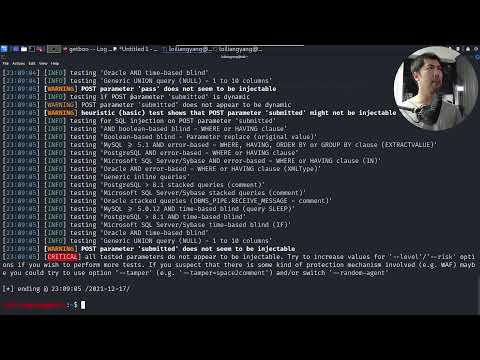
37,600 4.38%
222,000 4.18%
6,940 8.59%
108,000 2.8%
53,000 3.95%
661,000 2.65%
99,100 5.01%
99,500 4.8%
9,480 4.4%
3,030,000 1.43%
1,480,000 4.21%
821,000 2.8%
672,000 3.58%
10,500,000 3.02%
21,100 7.11%
13,700 2.85%
24,100 4.18%
32,400 2.19%
25,700 6.03%
17,600 5.24%
28,000 4.28%
26,200 2.38%
736,000 2.14%
132,000 5.03%
474,000 4.75%
8,890 3.66%