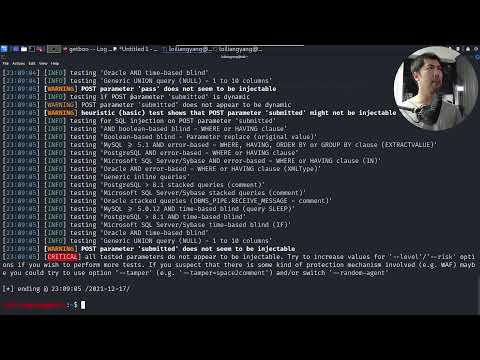
6,830 1.65%
801,000 3.01%
55,200 0.67%
474,000 4.75%
18,500 1.42%
36,800 1.76%
28,500 1.8%
17,000 2.98%
16,700 2.38%
22,100 1.09%
38,800 2.99%
8,760 0.53%
29,800 0.99%
49,200 0.69%
5,560 2.47%
389,000 3.77%
13,000 1.66%
46,000 1.08%
259,000 1.45%
760,000 1.68%
183,000 4.41%
31,100 2.39%
364,000 3.05%
9,550 3.16%
27,300 2.17%
132,000 5.03%