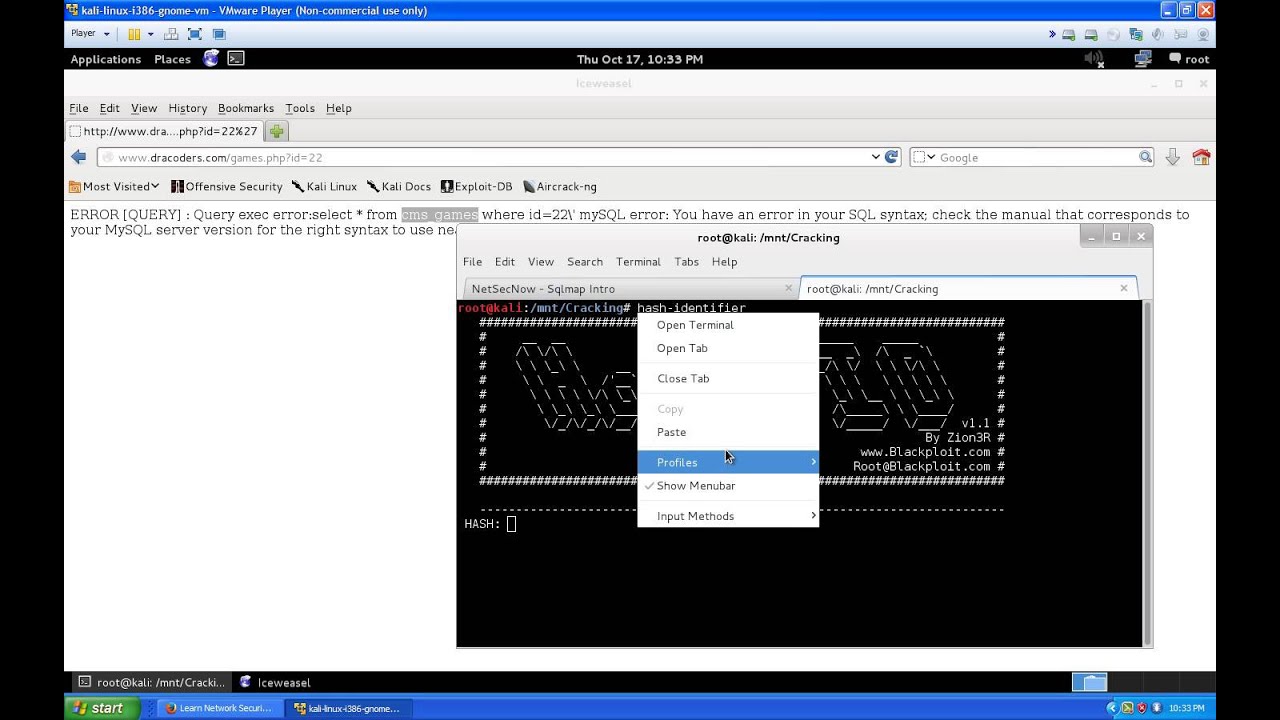
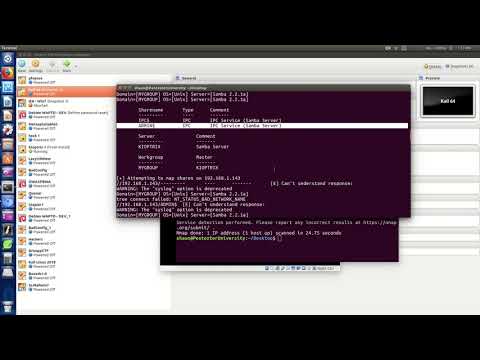
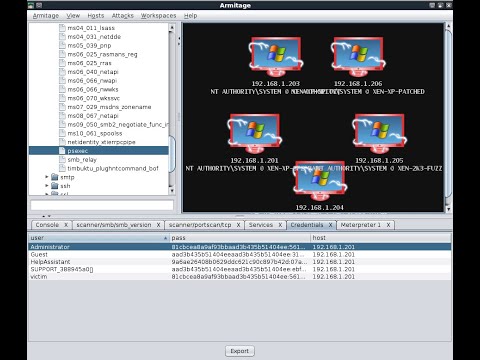
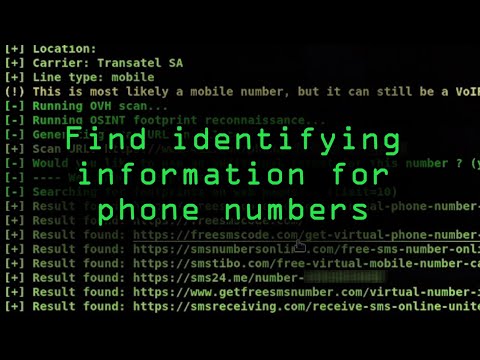
48,400 1.44%
801,000 3.01%
222,000 4.18%
20,000 2.56%
3,030,000 1.43%
247,000 1.43%
85,300 10.27%
819,000 4.25%
9,610 2.78%
10,300 2.07%
1,480,000 2.6%
9,160 4.99%
28,000 4.28%
187,000 3.82%
10,000,000 5.96%
25,900 2.85%
132,000 5.03%
63,400 1.8%
3,360,000 1.48%
1,540,000 2.64%
2,040,000 2.68%
106,000 1.24%
474,000 4.75%
661,000 2.65%
4,620,000 2.7%
50,300 1.38%