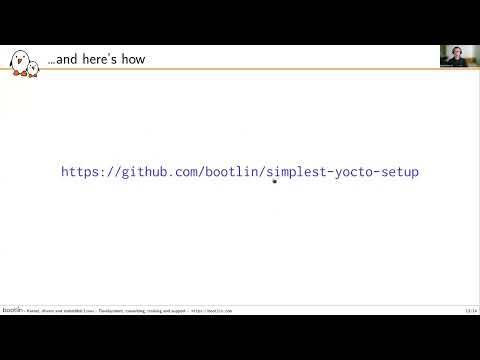
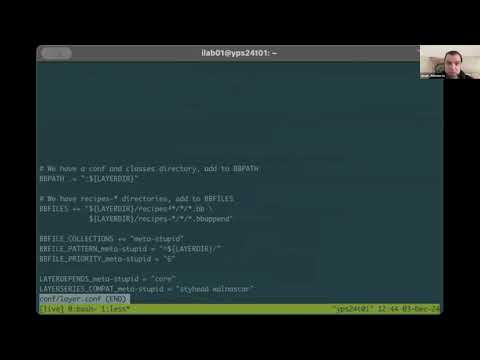
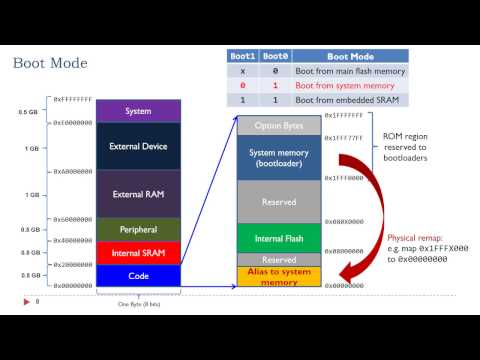
56,000 1.67%
672,000 3.58%
6,270 0.85%
40,100 6.64%
2,040,000 2.68%
37,600 4.38%
10,500,000 3.02%
6,820 1.29%
8,100 3.41%
14,700 2.35%
6,420 2.13%
6,980 2.85%
87,100 1.8%
90,400 2.26%
76,800 1.71%
53,700 1.56%
7,880 4.73%
21,600 1.48%
78,500 3.39%
553,000 1.21%
17,700 1.69%
121,000 1.21%
2,550,000 1.26%
108,000 2.8%
926,000 2.61%